Project information
- Category: Port scanning and cryptography
- Client: WomenTechsters
- Project date: July, 2021
- Project URL: https://github.com/rosa/nmap
Project Detail
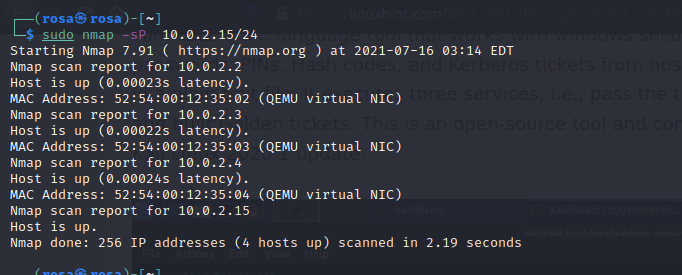
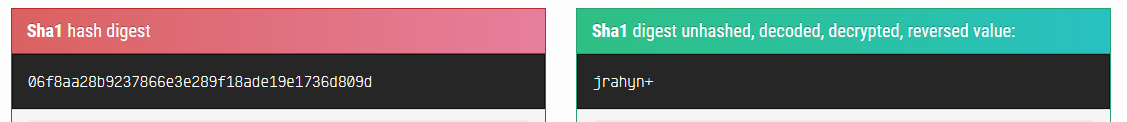
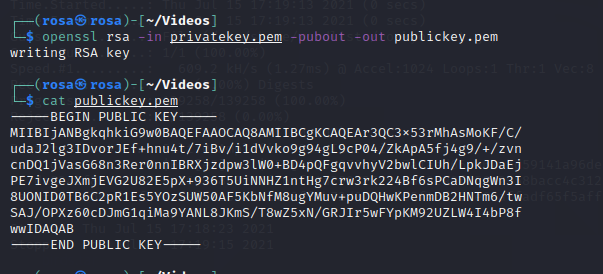
Performing various scans using nmap, analyzing results and determining areas that can be exploited. Cracking a hash. Performing encryption using openSSL.